Navigating Cybersecurity Challenges
Navigating cybersecurity for companies is challenging and can appear daunting for businesses that are just now stepping into the world of information security. Make sure you understand what is required to keep your business and customer data safe. Invest the time and resources into cybersecurity now will pay off in the long run.
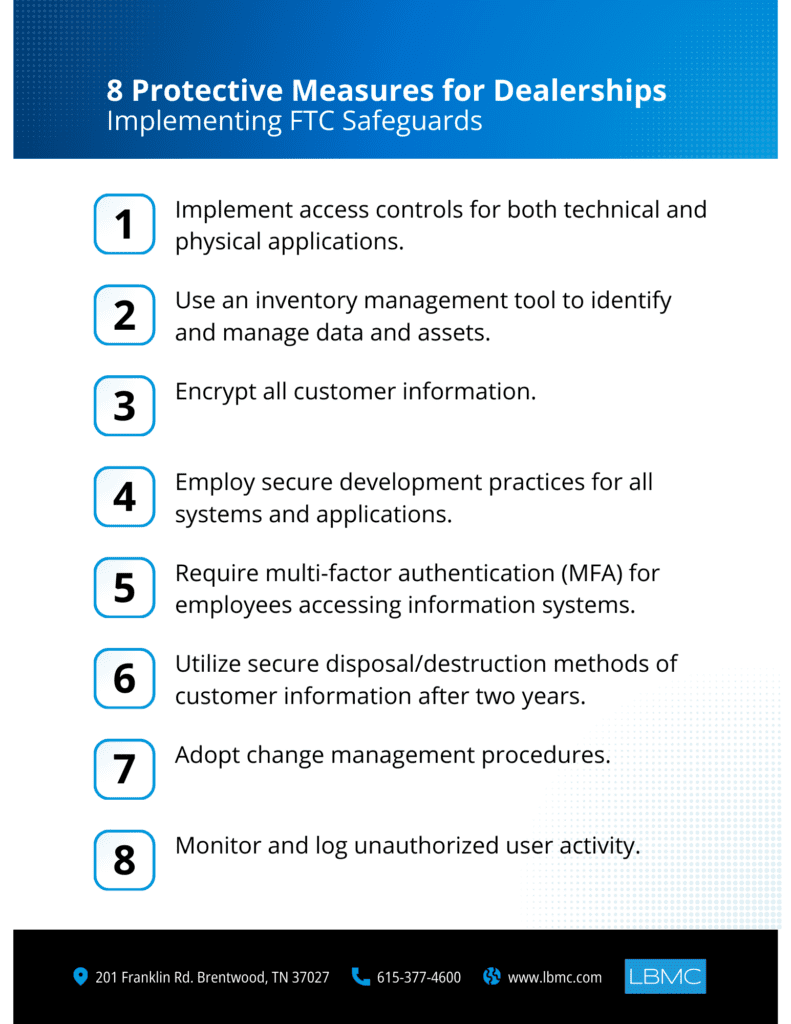
FTC Safeguards Rule
The Federal Trade Commission (FTC) put in place the Safeguards Rule to protect businesses against cyber risks and provide a baseline of security. The Safeguards Rule introduces several important requirements to ensure that all businesses that are “engaging in activity that is financial in nature” are compliant with the same security regulations as other financial institutions.
Who Must Comply
The FTC has mandated that all non-banking financial organizations comply with the rule. This includes automotive dealers, lenders, brokers, account servicers, check cashers, collection agencies, credit counselors, and travel agencies. By doing so, these businesses align with the security standards expected of financial institutions.
Exceptions for Small Businesses
It should be noted, however, that some exceptions do exist for companies that interact with customer information with fewer than 5,000 customers (16 CFR 214.6). Specifically, sections 314.4(b)(1), (d)(2), (h), and (i) do not apply which outline specific requirements as part of the requisite risk assessment and incident response plan.
Consequences of Non-Compliance
Failure to comply with the Safeguards Rule can result in fines and reputational damage with penalties able to reach $100,000 per violation. In addition, customers, employees, and third parties can sue businesses for violating a compliance standard that could have prevented a cyber incident.