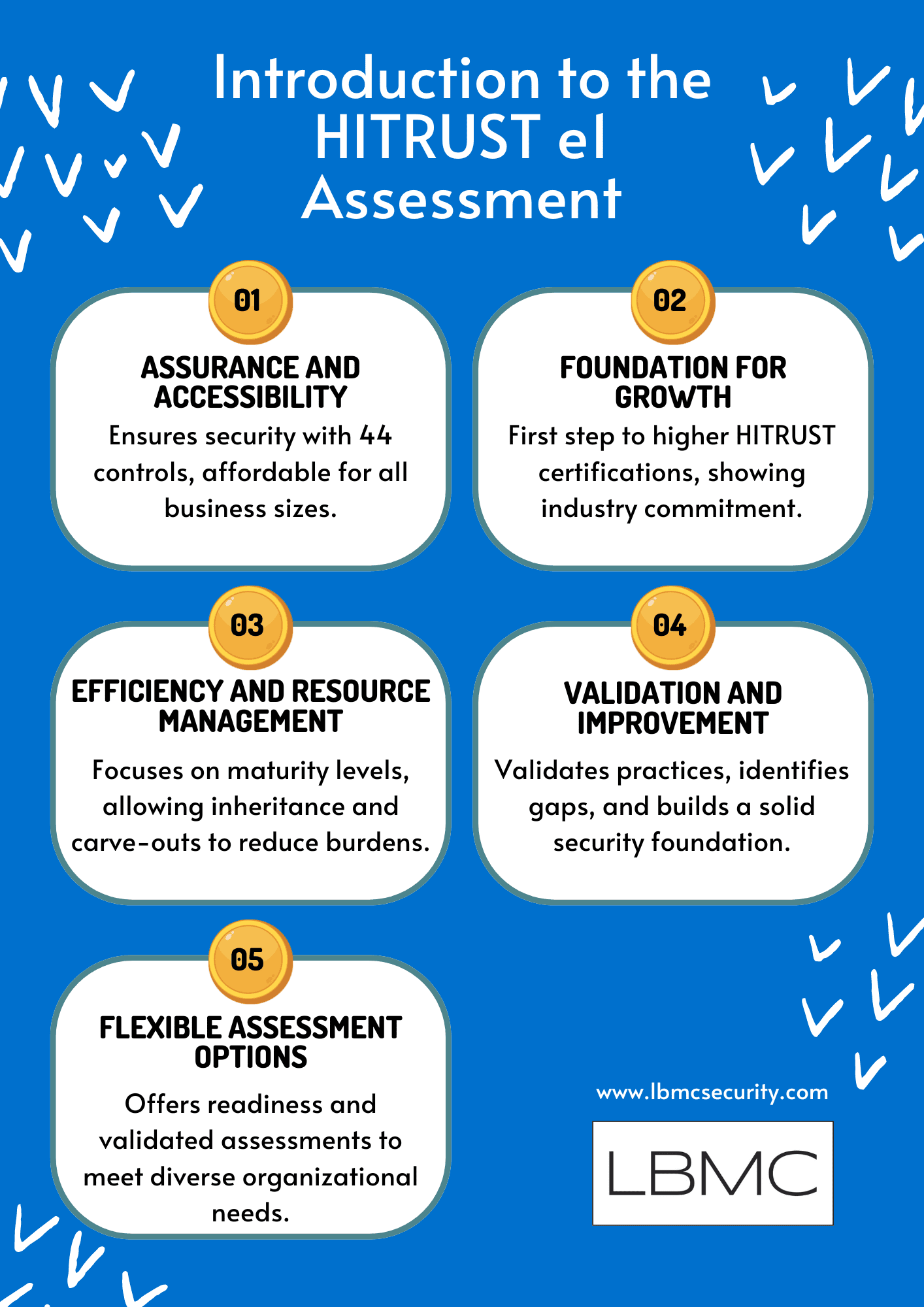
By zeroing in on the HITRUST implemented maturity level and allowing for both inheritance and carve out methods, the e1 reduces the assessment burden for your organization.
Implemented Maturity Focus
Unlike the more comprehensive r2 assessment, the e1 doesn’t segregate policies and procedures for separate testing and scoring; it instead integrates them into the overall evaluation. The e1 focuses on how well your organization has put security practices into action, testing one of the five HITRUST maturity levels, implementation. This approach is particularly valuable for businesses seeking a foundational understanding of their security posture.
While the e1 simplifies the assessment, it’s still essential to recognize that policies and procedures matter. They provide the framework for effective security practices. So, even though they aren’t scored independently, their alignment with implemented controls contributes to your overall security posture.
Inheritance and carve outs
Additionally, the e1 assessment offers the opportunity for both inheritance or the Carve-Out Method. Inheritance lets your company use security policies and procedures already in place elsewhere. Should your MSP or a partner company go through HITRUST evaluations, you can inherit their verified controls to expedites your assessment process. You build on the foundation others have laid instead of beginning from nothing.
If your organization relies on external vendors or partners for critical services (such as cloud hosting, payment processing, or data storage) and these third parties are not HITRUST certified themselves, the carve-out method is available. With carve-outs, you can isolate specific components of your environment that fall under third-party responsibility. These components are excluded from your assessment scope.
Carve-outs allow you to maintain e1 certification while acknowledging that certain aspects are handled externally. It’s a pragmatic approach that balances security and operational realities. For organizations collaborating with MSPs or relying on third-party services, these mechanisms reduce the burden of duplicative assessments. You can focus on what’s truly within your control while benefiting from existing security efforts.
Level of Effort and Resources
Compared to its more rigorous counterparts, the HITRUST i1 and r2 Assessments, the e1 assessment requires less effort to complete. It’s an easily available starting point for companies of all kinds since it balances offering significant assurance with reducing resource burden.
Based on our industry expertise, we compare the degree of lift to be roughly equivalent to a SOC 2 exam; e1 Readiness is most like a SOC 2 Type 1 and the full Validated assessment is most like a SOC 2 Type 2.
All in all, the HITRUST e1 Assessment empowers businesses by simplifying security evaluation, accommodating external partnerships, and optimizing resource allocation.