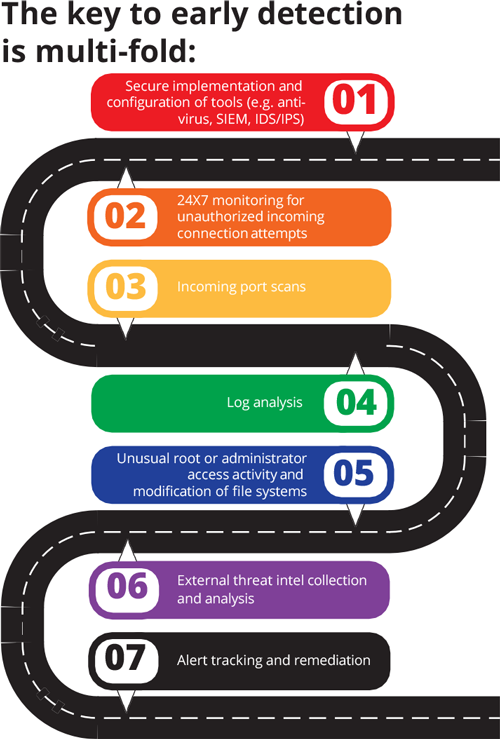
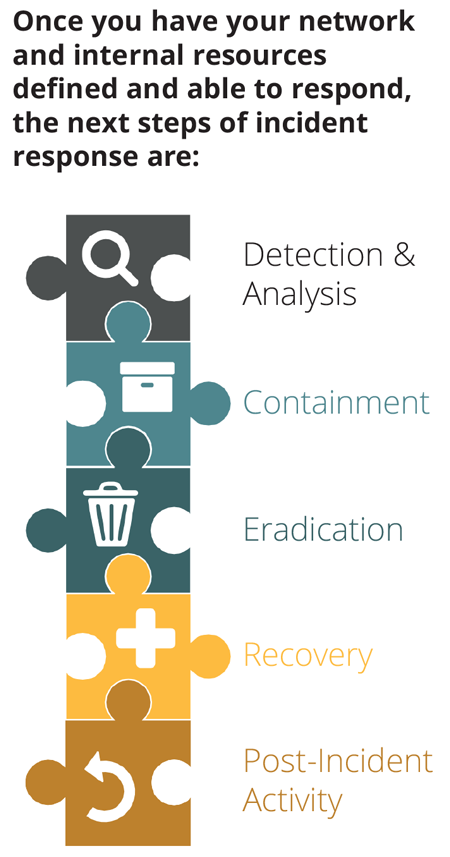
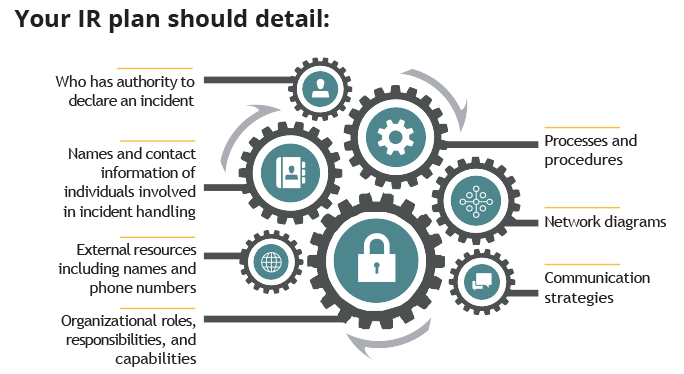
Having a comprehensive Incident Response Plan to guide your actions can be the difference between success and failure.
1. Containment
Don’t delay your response once an intrusion is identified. Do carry out your containment procedures with expediency. Containment strategies will vary, depending on the nature of the attack.
In some cases it will be appropriate to shut down affected systems quickly. In others, you will want to keep them up and closely monitor the attacker’s activities in order to gain additional detail that will be helpful during the remainder of the response.
2. Eradication & Recovery
Once the incident is contained, it’s time to start cleaning up the mess. During eradication, you will identify all affected systems and perform activities appropriate to the incident type, such as removing malware or changing passwords on breached user accounts.
Recovery activities typically involve actions like restoring files from backup, or installing missing security patches. These efforts are intended to get you back to normal business operations.
3. Post-Incident Activity & Communication
Notification of internal and external players: Don’t delay in communicating with internal departments and external vendors, partners and clients. Do outline a clear chain of communication before breach detection and follow it post-breach.
Depending on your industry and state, laws vary with regard to required deadlines to inform those affected by the breach. Following proper procedures carefully and quickly can minimize breach fallout.
Remember to contain the breach, gather your response team, and thoroughly investigate the incident. Document all details—who, what, where, when, why, and how—along with notification deadlines. Follow your communication procedures by informing authorities, insurance companies, and those affected. Finally, assign a network security team leader to oversee and update the Incident Response Plan regularly.